Home Lab – Detection & Response Environment
My personal cybersecurity lab is built for hands-on cybersecurity practice: log analysis, packet inspection, detection engineering, threat hunting, and incident response simulation.
Current Hardware
- Dell OptiPlex 7050 Micro – Primary Lab Server
Intel Quad Core i5-6500T up to 3.1 GHz • 16 GB DDR4 • 256 GB SSD • Windows 11 Pro 64-bit - Lenovo ThinkPad T480 – Management & Analysis Laptop
Intel Core i5-8350U • 16 GB RAM • 256 GB SSD • Windows 10 Pro - Netgear GS308 – 8-Port Gigabit Unmanaged Switch
Network Topology
High-level overview of the current homelab layout:
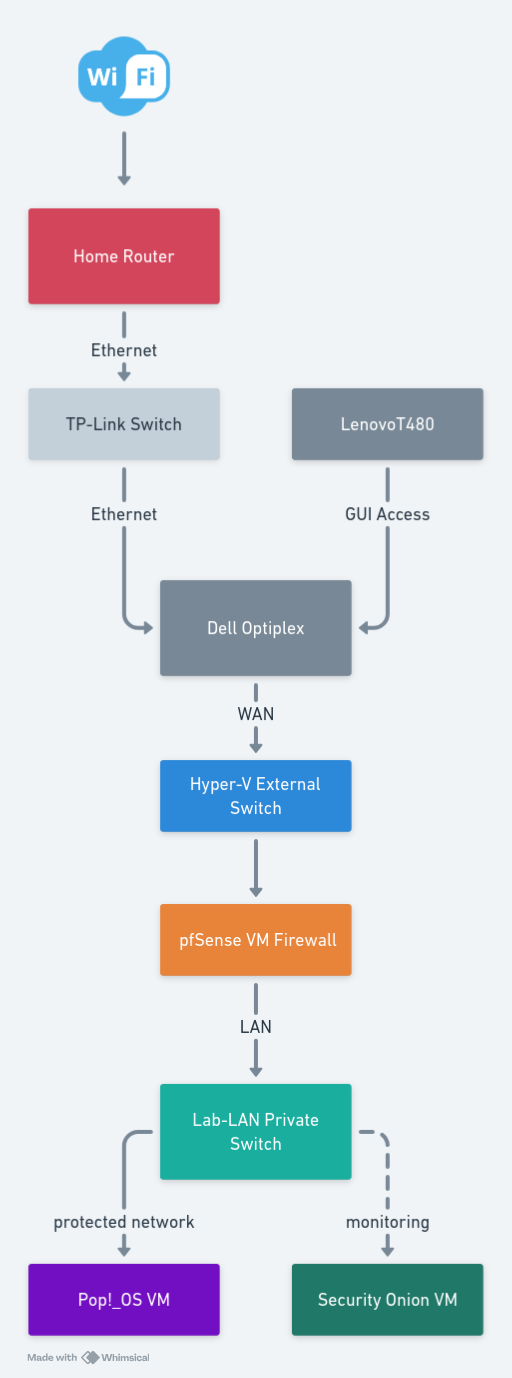
Summary of current setup:
- Lenovo ThinkPad T480 – Management & analysis laptop (Windows 10 Pro). Used for browser access to VM dashboards.
- Dell OptiPlex 7050 Micro – Primary lab server (Windows 11 Pro + Hyper-V).
- Single physical Ethernet → TP-Link unmanaged Gigabit switch → home router (internet).
- Hyper-V virtual switches:
- External switch – bridged to physical Ethernet (WAN/internet)
- Lab-LAN private switch – isolated internal lab network
- Virtual machines on Dell:
- pfSense VM – Firewall/router (WAN → External switch, LAN → Lab-LAN)
- Pop!_OS VM – Lab workstation (protected via pfSense)
- Security Onion VM – Network monitoring & intrusion detection (passively monitors Lab-LAN traffic)
All lab traffic flows through pfSense for protection and NAT. Security Onion provides visibility and detection across the isolated Lab-LAN network. The Lenovo laptop is used to manage everything via web GUIs.
Core Tools & Platforms
- Security Onion – Full packet capture, IDS, log management
- Splunk Free – Log ingestion and dashboarding
- Wireshark – Deep packet analysis
- Velociraptor / Elastic Agent – Endpoint collection
- Sigma Rules – Cross-platform detection logic
- Kali Linux VM – Controlled adversary emulation
- Atomic Red Team – Safe technique testing
Daily Lab Activities
- Full packet capture and long-term storage
- Log forwarding from Windows, Linux, and network devices
- Writing and testing custom Sigma detection rules
- Threat hunting exercises with real malware samples (in isolated VMs)
- Building and tuning Splunk dashboards
- Practicing incident response workflows and documentation
- Experimenting with new open-source security tools
Goals of This Lab
Stay sharp on real-world detection techniques, deepen tool proficiency, contribute detection content (Sigma rules, scripts), and continuously improve my ability to protect and respond — all in a safe, isolated environment.
Useful Links
- Security Onion – securityonion.net
- Splunk Free – splunk.com
- Sigma HQ – github.com/SigmaHQ/sigma
- Atomic Red Team – redcanary.com/atomic-red-team
Last updated: January 2026